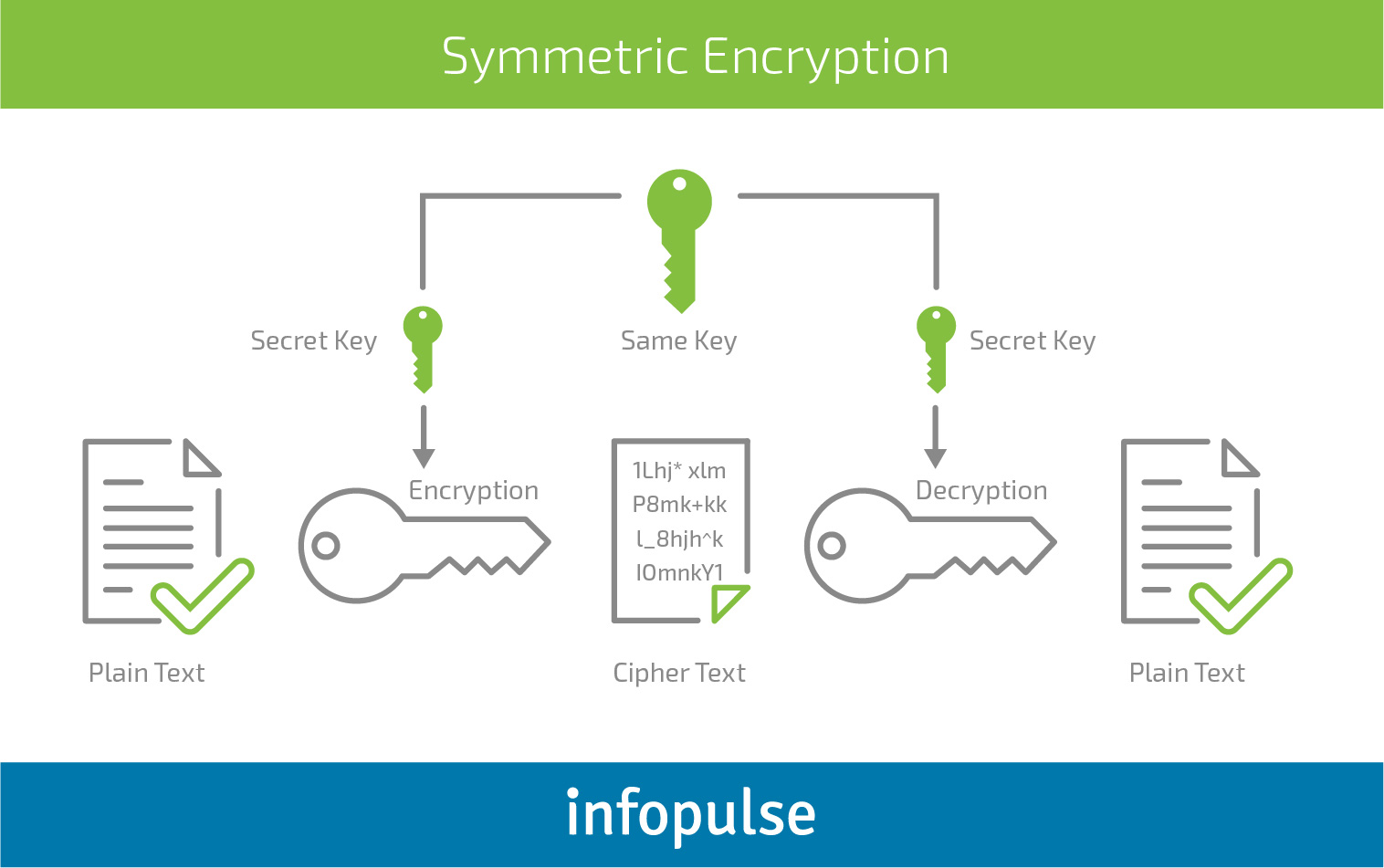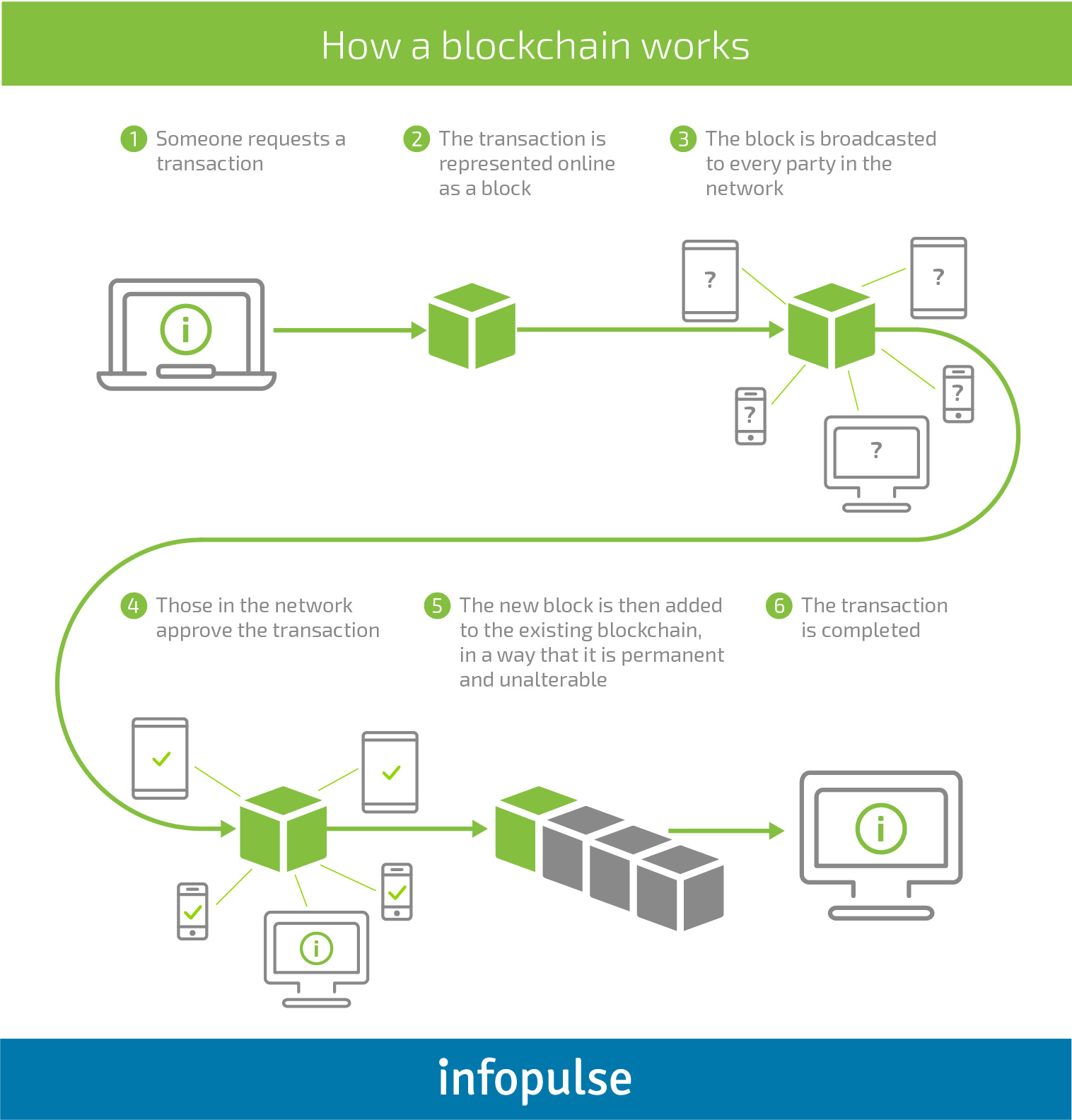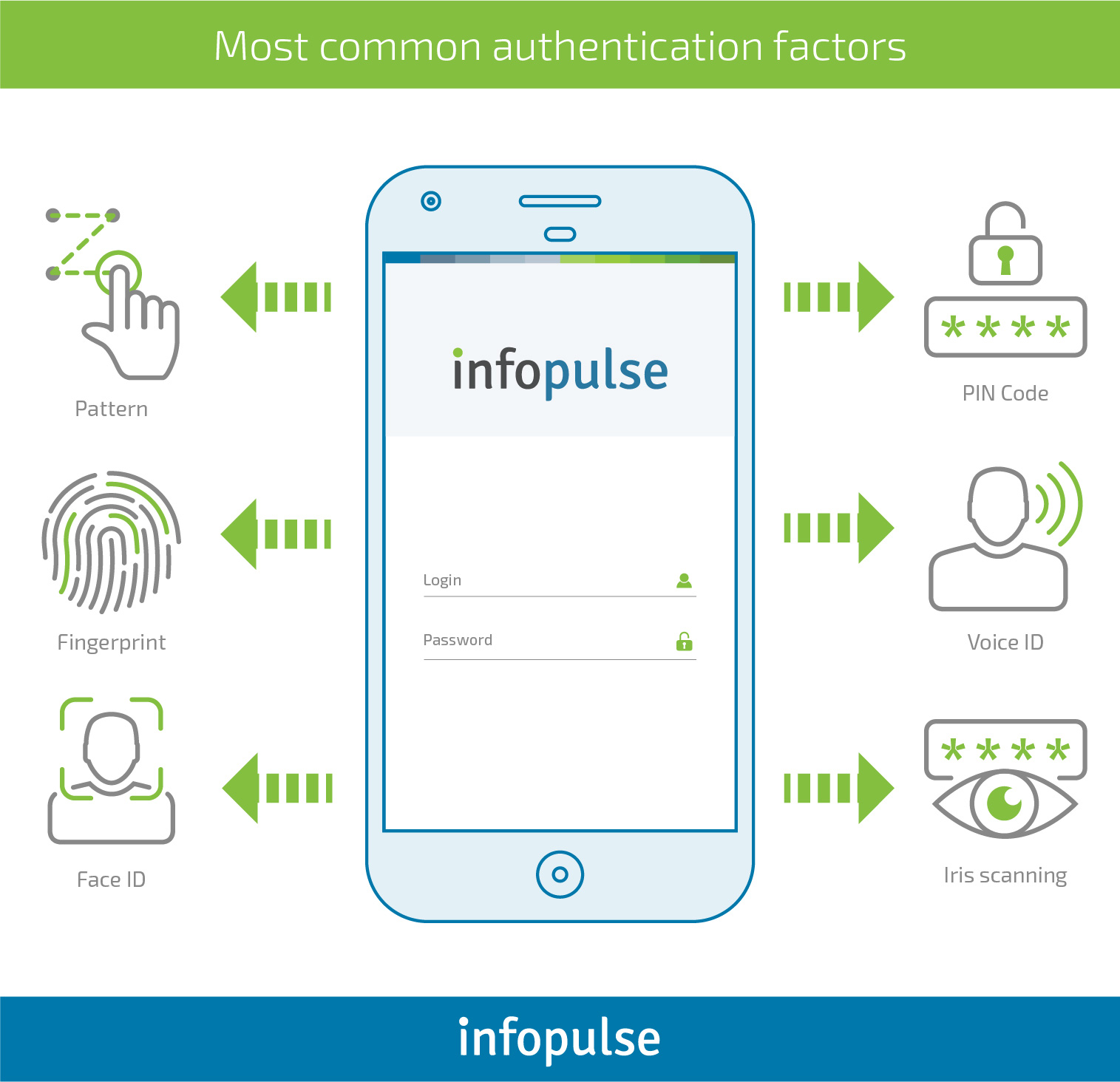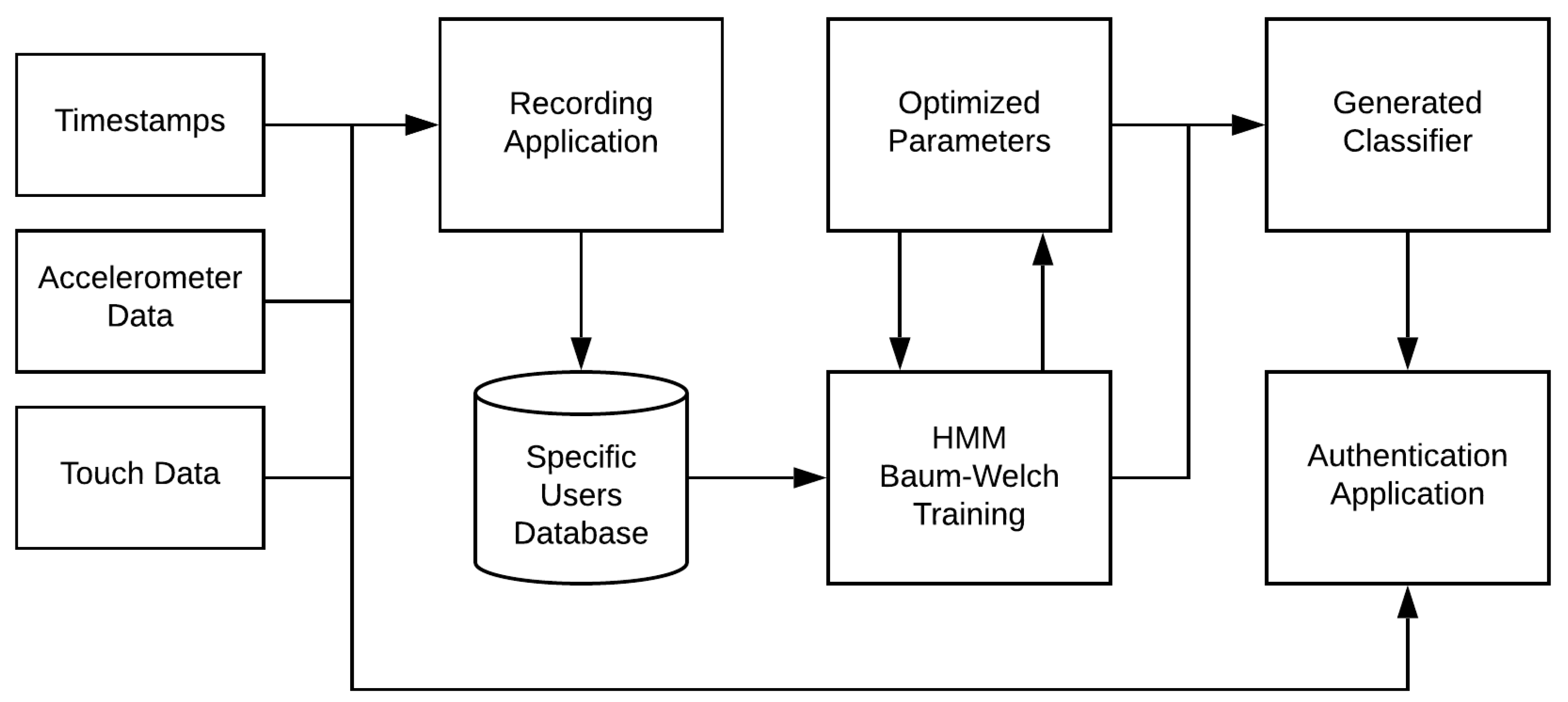
Applied Sciences | Free Full-Text | Continuous Mobile User Authentication Using Combined Biometric Traits

Ways to Implement Multifactor Authentication System during Mobile App Development - Inficaretech Blog

Zoloz biometric authentication system compliant with ISO presentation attack detection standard | Biometric Update
GitHub - nays12/QRCode-Authentication-Mobile: Mobile Token Application component of the QR Code Mobile Authentication System

Fingerprint Authentication System for Smartphone and Cloud Computing Stock Illustration - Illustration of cellphone, control: 41352891

Fingerprint Authentication System for Smartphone and Cloud Computing Stock Illustration - Illustration of mobile, internet: 41352890

A Secure and Privacy-Preserving Mutual Authentication System for Global Roaming in Mobile Networks | SpringerLink
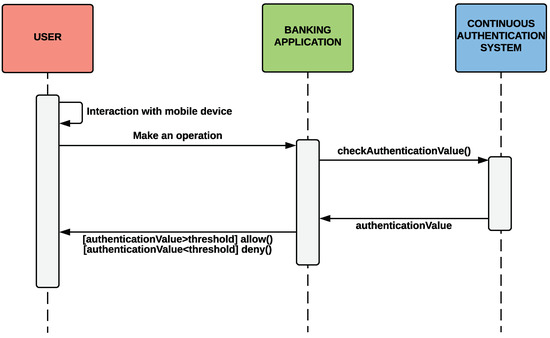
Sensors | Free Full-Text | Improving the Security and QoE in Mobile Devices through an Intelligent and Adaptive Continuous Authentication System
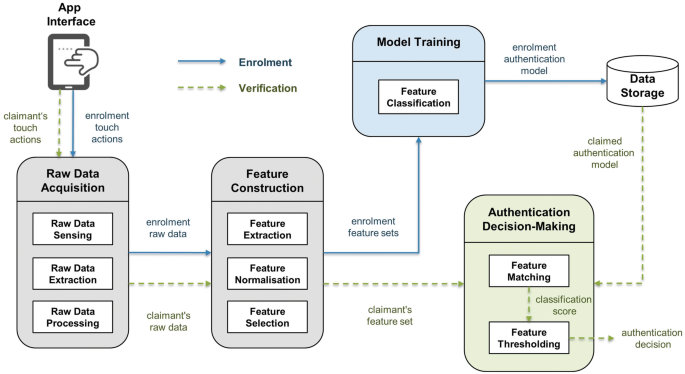
Strengthen user authentication on mobile devices by using user's touch dynamics pattern | SpringerLink